Blind OS command injection -Portswigger (LAB-2) | INFOCODX
Hey there, how are you all? I hope everything is going smoothly and everyone is doing fine. Today, we're diving into the exciting world of OS Command Injection labs from portswigger. Get ready for some hands-on action!
So what is blind OS command injection?
I've already covered OS command injection in my previous blog post. Blind OS command injection works similarly, but instead of receiving output back to the web app, we don't get any output. So, how can we determine if there is a blind OS command injection? One technique is to use time delay. By using an OS command that takes some time to execute, we can test for it.
LAB 2 : Blind OS command injection
When we access this lab, a web application will be presented to us. As shown below, there is a feedback form available for submission.
Firstly, let's go ahead and explore that particular feature, utilizing it to conduct a thorough analysis. It's worth noting that there is a dedicated functionality allowing users to submit their valuable feedback. Now, let's delve into the workings of this feedback form. To better understand its functionality, I decided to input a random value into the form and submit it. Subsequently, I captured the request on the burp suits for further analysis.
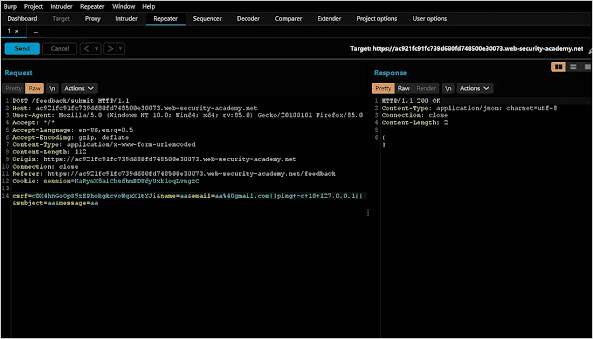
When we analyze the feedback form in burp suite, we notice that there are several parameters being passed along with user input. It is crucial for us to thoroughly test all of these parameters for potential command injection. Since this lab focuses on blind command injection, we need to perform tests using a command that takes some time to execute. This way, we can confirm if our command has been successfully executed.
When it comes to detecting blind OS command injection, the ping command is a valuable tool. By sending a minimum of 10 packets, it will take some time to complete, giving you the opportunity to assess the situation. I initially attempted using the name parameter, but unfortunately, it didn't work. However, when I switched to the email parameter, we were able to achieve the desired output due to the lack of proper user input validation.
command : ping -c 10 127.0.0.1
The picture below clearly shows that our lab is solved when we send the request and it performs exactly as expected.
Hooray!!!!! We've made it! I hope you've found something valuable by dedicating your time to this. If you have any uncertainties, feel free to leave a comment.
Happy hackers!!








Comments
Post a Comment